Citrix DaaS (Workspace Extension)
Overview
For Citrix delivered Desktops, the Workspace Extension allows Active Citrix sessions to be viewed and terminated from within Atria. This enables Service Provider service desk, Resellers and End-Customer administrators to support end-users without requiring administrative access to Citrix servers.
This works in conjunction with the Workspace Service. The Workspace service manages configuration of the User, and assignment to groups to control the Desktop Experience. The Citrix DaaS extension adds features specifically for Citrix.
This feature works with:
- Citrix Cloud (multi-tenant or Private).
- Citrix Virtual Apps and Desktops.
Citrix DaaS is implemented through the Atria Service - "Citrix DaaS" which must be installed and provisioned to the customer. Citrix DaaS is dependent on the Workspace service. This means Workspace must be enabled and provisioned to the customer prior to Citrix DaaS being enabled.
System Requirements
- Citrix Daas (Citrix Cloud), multi-tenant or private cloud, or
- Citrix Virtual Apps and Desktops (Min Version 7 2308)
- Atria environment with Workspace Service deployed
Features by User Role
Service Provider/Reseller Admin
- View active sessions for individual tenants, regardless of whether they are in Citrix Cloud Multi-tenant, private tenant, or on-premises.
- Seek and force log-off end-users from sessions, without needing to find/login to any external system.
- Audit trail of any forced log off events. Who logged the user off and when they did it.
End-Customer Administrator
- View active sessions for all users within their customer.
- Force logoff any users session
- Audit trail of any forced log-off events
End-User
- Users provisioned with WorkSpace can also Login, view their own sessions and force-logoff their own session.
Deployment
Atria uses the Citrix REST API to access session information, this is available both on Citrix Cloud and in recent releases of Citrix Virtual Apps and Desktops.
Firewall Configuration
Atria needs to be able to make outbound calls to the Rest API to retrieve session information.
- Atria Provisioning Server to Citrix REST API (HTTPS Traffic)
Deployment Process
The user performing this task, must have Atria Service Provider Administrator permissions. Enabling this service carries low risk to existing operations.
Enable the Service
- Login to the Atria portal
- Ensure that the Atria Workspace service has already been deployed and enabled.
- Enable the Citrix DaaS Service at both the Top Environment Services and Active Directory Location Services
- Navigate to
Configuration > System Manager > Service Deploymentand expand Citrix Daas.
Service Deployment
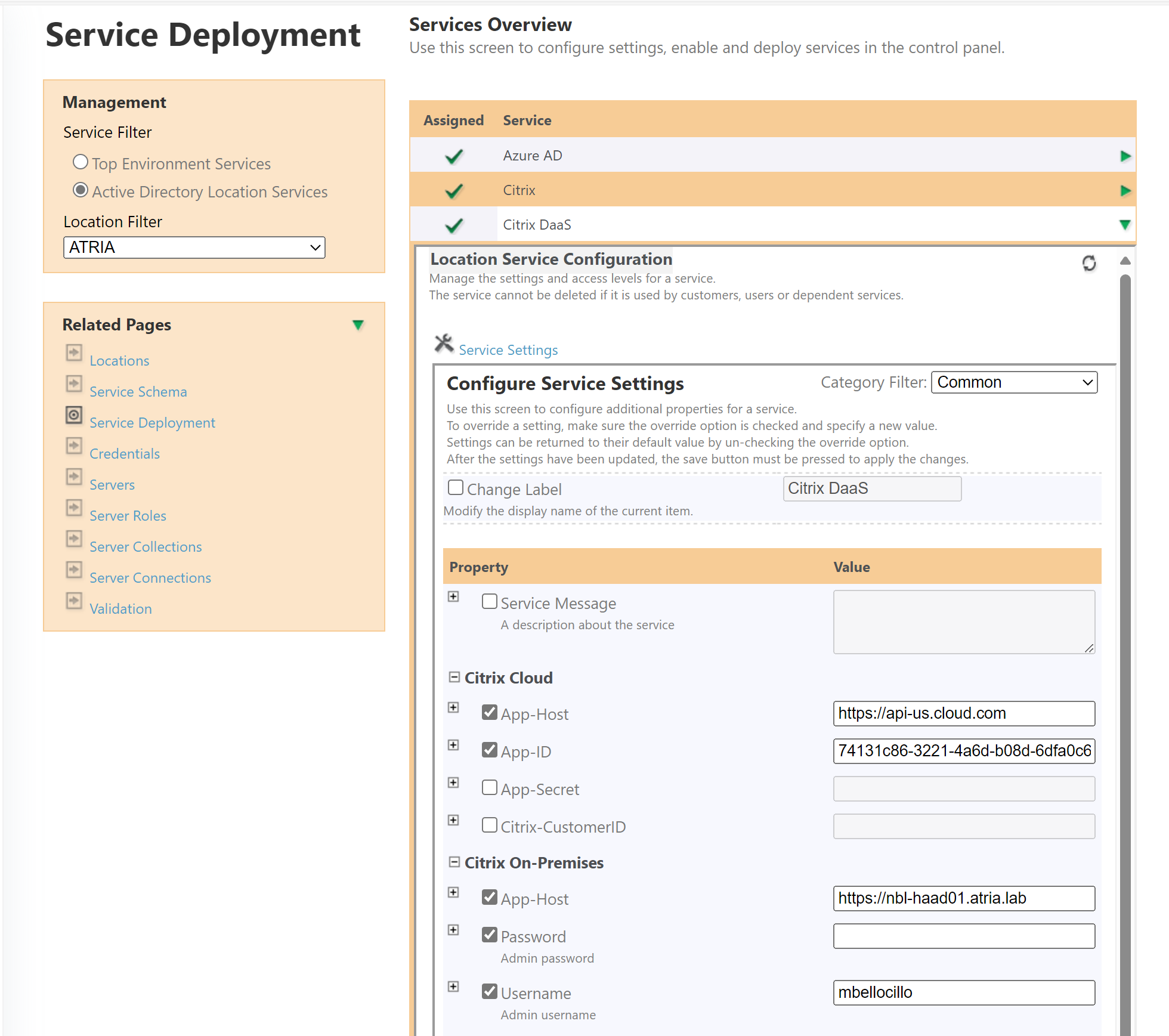
Follow the section below which describes your Citrix setup.
- Citrix Cloud - Multi-Tenant
- Citrix Cloud - Private Tenant
- CVAD - Multi-Tenant
- CVAD - Private Tenant
Configure the Service
- Ensure the Atria Provisioning Server is able to reach the Citrix Cloud API with HTTPS traffic
- Set up API access tokens : Follow the guide Get started with Citrix Cloud APIs | Citrix Cloud API overview to get your API access configured. Follow this guide, and take note of the ID, Secret and API URL.
- Set the
App-hostto the API URL Citrix Cloud API URL - e.g. https://api-us.cloud.com - Set the
App-IDandsecretvalues to the ID and Secret from your Citrix Cloud API Client. - Leave the values under
Citrix On-Premisesblank
- Save the Service Configuration
- Navigate to the Root Customer, In the Reseller Service, enable the Citrix DaaS service with default settings.
Properties marked as secret cannot be viewed after they are set. This applies to the API secret and passwords.
If you are re-editing this page, then the Password must be re-entered otherwise it will be blanked out and Api access will fail
-
Click Save when finished.
-
Locate the Citrix Cloud TenantID:
- Each Tenant within Citrix Cloud has a TenantID – this is an alphanumeric string, an example is : s4x90ic0lutv
- Atria needs the TenantID in order to accurately segregate session data.
- To locate the TenantID, log into Citrix Cloud, Go to the Customer Dashboard, locate the customer, select the Ellipsis and click on View Details:
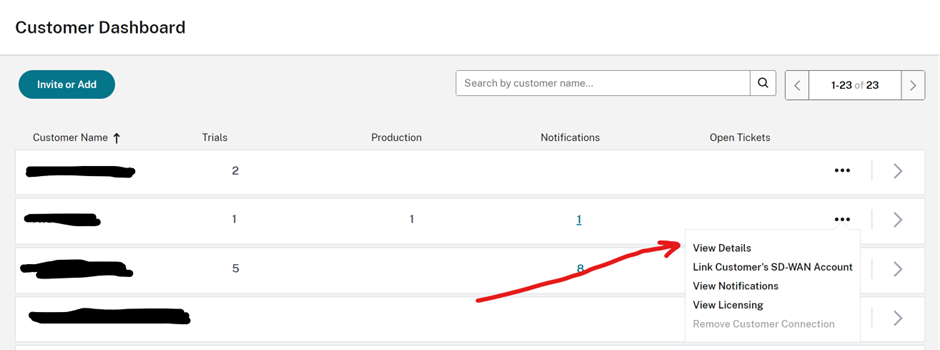
- The Customer Details page will be shown, the TenantID is embedded in to the URL:
https://us.cloud.com/customeraccount/{tenantID}/information
- Locate the tenantID from the URL and Copy.
- Enable at Customer Level:
- Locate the customer, expand the Citrix DaaS service, enter the TenantID for the customer, and provision.
You should now be able to view sessions for the customer.
Configure the Service
-
Ensure the Atria Provisioning Server is able to reach the Citrix Cloud API with HTTPS traffic
-
Set the default API URL to use for all customers. If you have customers in different Citrix Regions, you can override this at Customer Level, or configure a separate Atria Location to handle that region.
-
Click Save when finished.
-
Navigate to the Root Customer. In the Reseller Service, enable the Citrix DaaS service with default settings.
-
Enable at Customer Level:
- Create API credentials for each individual tenant:
-
Set up API access tokens : Follow the guide Get started with Citrix Cloud APIs | Citrix Cloud API overview to get your API access configured. Follow this guide, and take note of the ID, Secret and API URL.
-
Locate the customer and expand the Citrix DaaS service. Under Service Settings:
- Set the
App-hostto the API URL Citrix Cloud API URL - e.g. https://api-us.cloud.com App-IDandsecretset to the ID and Secret from your Citrix Cloud API Client.- Leave the values under
Citrix On-Premisesblank - Save and Provision the service. You should now be able to view sessions for the customer.
- Set the
-
Properties marked as secret cannot be viewed after they are set. This applies to the API secret and passwords.
If you are re-editing this page, then the Password must be re-entered otherwise it will be blanked out and Api access will fail
Configure the Service
Citrix CVAD configuration requires a URL and AD credentials of the user account under which the API calls are made, Atria uses the credentials to generate a bearer token, this is then presented to access the API.
- Ensure the Atria Provisioning Server is able to reach the Citrix Cloud API with HTTPS traffic
You might have to place the Api Servers Server Certificate onto the Provisioning Server before the Certificate can be verified
-
Enter the following details under Citrix On-Premises:
- Under
APP-Host- specify the URL to Citrix API, this must be resolvable and accessible from the Atria Provisioning server. - Enter Citrix API credentials into the
UsernameandPasswordfields. - Leave the values under
Citrix Cloudblank - Click Save when finished.
- Under
-
Navigate to the Root Customer. In the Reseller Service, enable the Citrix DaaS service with default settings.
-
Enable at Customer Level:
- Locate the customer, expand the Citrix DaaS service, click Save and Provision. You should now be able to view sessions for the customer.
You do not need to specify a Citrix Cloud TenantID for an on-premises deployment.
Configure the Service
Citrix CVAD configuration requires a URL and AD credentials of the user account under which the API calls are made, Atria uses the credentials to generate a bearer token, this is then presented to access the API.
For a Private Tenant, the Citrix Api Server is in a different Environment (domain) than the Atria Servers. In this scenario, the Citrix Api needs to be accessed through Atria's queueing system (RabbitMq).
- Ensure the Atria Provisioning Server is able to reach the Citrix Cloud API with HTTPS traffic
You might have to place the Api Servers Server Certificate onto the Provisioning Server before the Certificate can be verified
- Navigate to the Root Customer. In the Reseller Service, enable the Citrix DaaS service with default settings.
- Navigate to the Customer's Citrix DaaS Service
- Enter the following details under Citrix On-Premises:
- Under
APP-Host- specify the URL asHttps://AtriaHttpTunnel:8101/Tunnel/{ComponentName}/{CustomerId}-
Where {ComponentName} is an alias for a Component Name. This can be any alphanumeric value that you like. For example CitrixCvad
-
And {CustomerId} is the Tenants CustomerId from Atria
The App-Host Uri may look like this:
Https://AtriaHttpTunnel:8101/Tunnel/CitrixCvad/27
-
- Enter Citrix API credentials into the
UsernameandPasswordfields. - Leave the values under the
Citrix Cloudsection blank
- Under
- Click Save and Provision when finished.
You do not need to specify a Citrix Cloud TenantID for an on-premises deployment.
Configure the Api Connection Details
In the Private Location (on the Provisioning Server), run the following in an Administrative Powershell window:
Set-AtriaSecret -SecretKey 'Tunnel:{ComponentName}' -SecretValue '{"Port":443,"UserDomain":"<domainname>","Hostname":"<fqdn-servername>","Username":"","Password":"","UrlBase":"/","Protocol":"https"}' -UseEnvironment
- Replace the <domainname> and <fqdn-servername> values.
- Leave the Username and Password blank
Private AD Atria Location
This applies when each customer has their own Active Directory and Citrix infrastructure.
In this scenario, all configuration (API URL, Username, Password) should be configured under the Citrix DaaS service at the Customer Level when assigning the customer the Citrix DaaS service.
Additional Notes
Dual configuration
Atria will collate and show sessions from both Citrix Cloud and Citrix CVAD.
If a customer has users split between Citrix Cloud and CVAD environments, the session viewer will consolidate data from both sources.
To configure, enter the details for both on-premises and Citrix Cloud.
If you are NOT using Citrix Cloud, do not specify values in the Citrix Cloud area of the Service Settings. If values are specified, Atria will attempt to retrieve session data from Citrix Cloud which will result in errors or slow performance.
Differences between Citrix Cloud and On-Premises:
With Citrix Cloud, Atria will retrieve all users and segregate them based on the TenantID. All users with sessions will be displayed, regardless of whether they have been provisioned into Atria.
With CVAD, filtering is based on the user identity within Atria, if the user is not provisioned in Atria, you will not be able to view their sessions in the Session viewer.