Identity Management
Overview
An Atria customer typically has a relationship with a Microsoft Active Directory instance. Atria Locations and Environments manage this relationship and configure the services that customers can consume.
An Environment in Atria is synonymous with an Active Directory Forest and defines where users will be created. Each Atria customer is associated with a single Environment, where their users are provisioned.
Locations control, segregate, categorize, and define services. Locations specify whether customers are contained within private Active Directories or exist within a shared Active Directory.
Locations
A location specifies the underlying Active Directory architecture, the default service configurations, and the network location of associated resources (such as server addresses).
The following diagram summarizes the types of locations in Atria. The Location Type defines the architecture used when associating customers with a location.
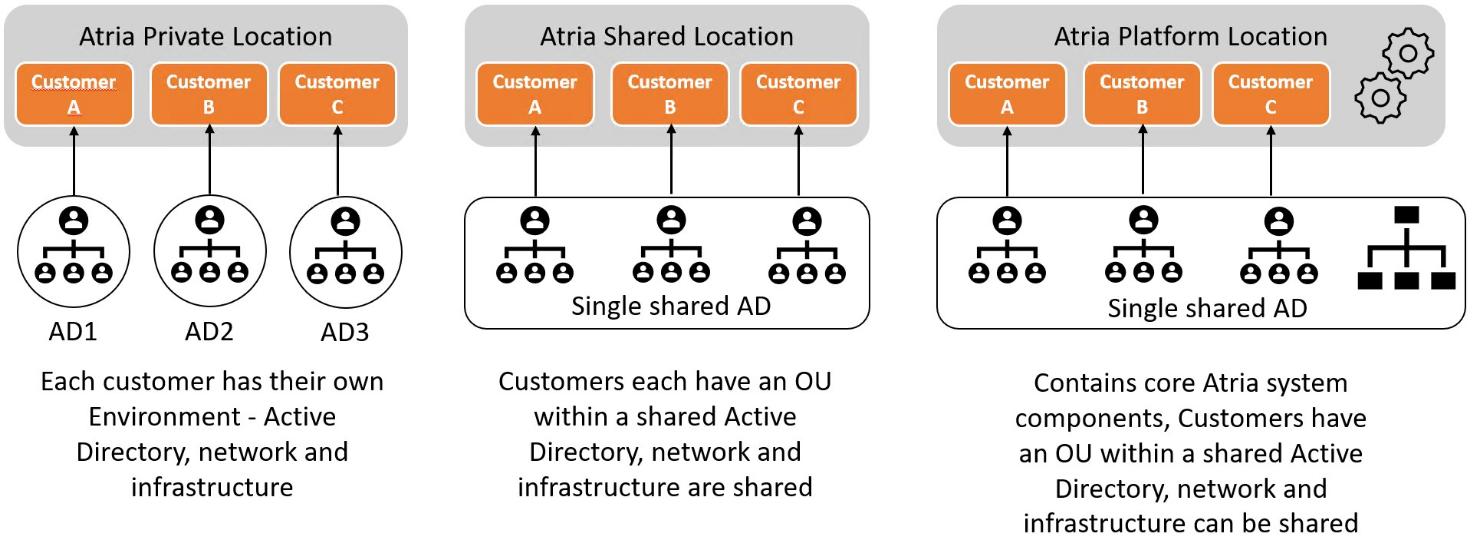
Private Locations
A Private Location can also have multiple customers, but each customer has its own "Private" Environment, meaning each customer has its own private Active Directory infrastructure.
Shared Locations
A Shared Location can have multiple customers. It has a single Environment specifying the Active Directory where customers are created. Each customer provisioned into this location will:
- Be associated with the Environment.
- Have an Organizational Unit (OU) created within the Environment's Active Directory.
- Provision all users into the customer’s OU.
Platform Locations
A Platform Location is a type of shared location created during installation. It has an Environment that maps to the Active Directory where Atria is installed.
Each Location can be enabled for one or more Atria services. Customers provisioned into a location can be assigned any of the services that have been enabled in that Location.
Location Scenarios
Managing Multiple Customers with Private AD Infrastructure
Managed Service Providers often support customers with private infrastructure. In these cases, each customer has its own private Active Directory. A "Private Location" must be added to manage these customers. The location's configuration controls the services available to these customers.
When a customer is in a Private Location, Atria seamlessly routes interactions with the customer's infrastructure to the correct Active Directory.
High-level Process:
- Add a new private location, e.g., "Private AD Customers."
- Define the services available in this location, e.g., "Workspace" or "Microsoft Online."
- Enable resellers to sell into this location via a reseller service for the new "Private AD Customers" location.
- Resellers can create new customers in Atria and download a script to install the Atria Agent into the customer's Active Directory.
ISV Isolated Infrastructure
Independent Software Vendors (ISVs) can deliver Windows applications through platforms like Citrix Virtual Apps and Desktops. For smaller volumes of users, it may be more economical to deliver applications from a single shared Active Directory.
By setting up a new "Shared Location," ISVs can resell into this location while being granted access to their own infrastructure. Provisioning can be fully automated, and new customers will be created in the Active Directory associated with this shared location.
For further information on locations and setting up remote environments, navigate to: Setting up a Remote Environment.
Network Communications
Atria uses RabbitMQ messaging middleware to streamline network communication between Atria and managed systems. The Agent installed in each Active Directory makes an outbound connection to the RabbitMQ service, listens for messages, and processes relevant actions. Atria sends messages, which are routed and handled by the appropriate environment, returning a response after processing.
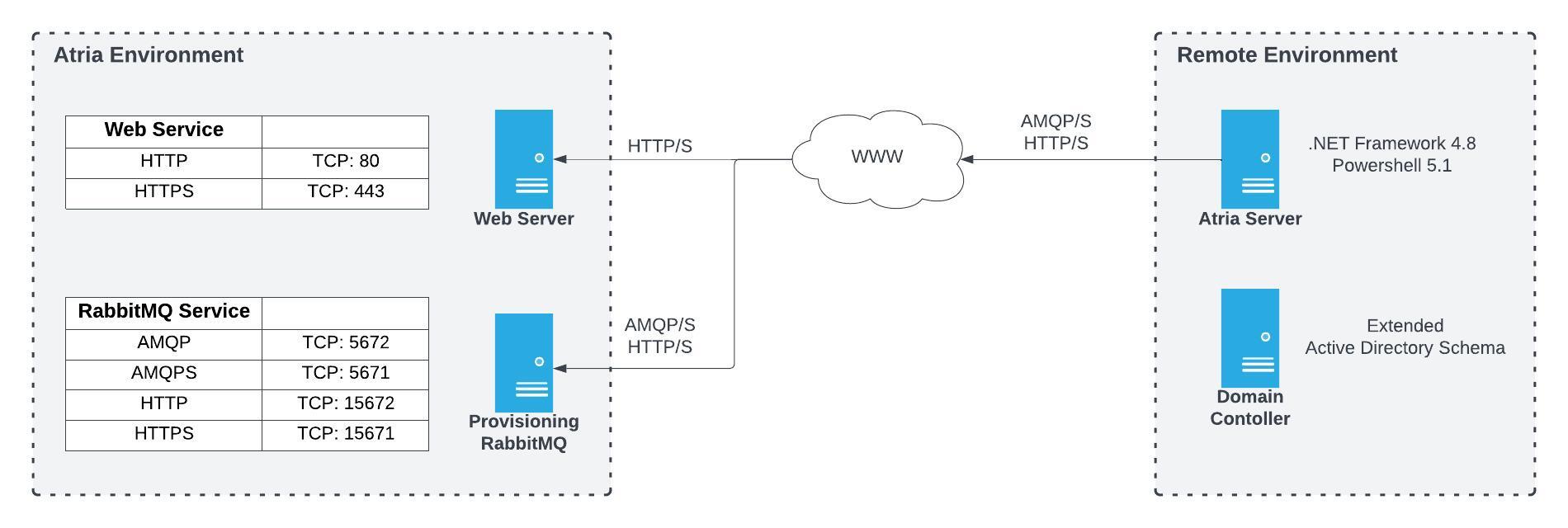
This infrastructure allows the Atria portal to initiate real-time requests, such as user authentication, or queue processes like user creation.
Multi-Tenancy of Active Directory
In some scenarios, multi-tenanting Active Directory provides significant efficiency by:
- Sharing core infrastructure, eliminating the need for dedicated AD servers.
- Enabling process automation using existing infrastructure.
- Enhancing operational efficiency through higher availability and centralized management.
In a shared location, Atria isolates individual customers within an Active Directory by:
- Creating an OU for the customer (e.g.,
{Customer Name} ({CustomerShortName})). - Creating a private group for the customer (e.g.,
{CustomerShortName} Proxy Users), and granting permissions to access their own OU. - Automatically adding users to the customer's private group and creating them within their own OU.
This solution is ideal for:
- ISV application delivery (e.g., desktop accounting solutions like QuickBooks).
- Standardized desktops/services for industry sectors.
- Hosted email services (e.g., Microsoft Exchange hosting).
- Access control for shared platforms, such as virtual server delivery solutions.
Platforms like Citrix Virtual Apps and Desktops or Microsoft Remote Desktop Services work seamlessly within an Atria-managed multi-tenant directory.
OU Hierarchy
For multi-tenancy setups, you can customise the hierarchal setup for Active Directory, giving you control over your structure.
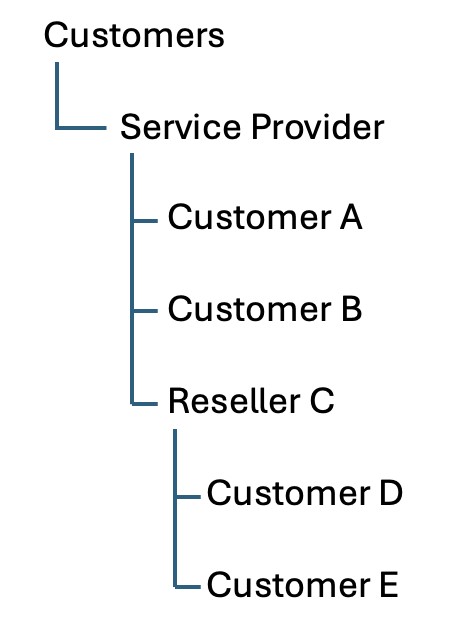
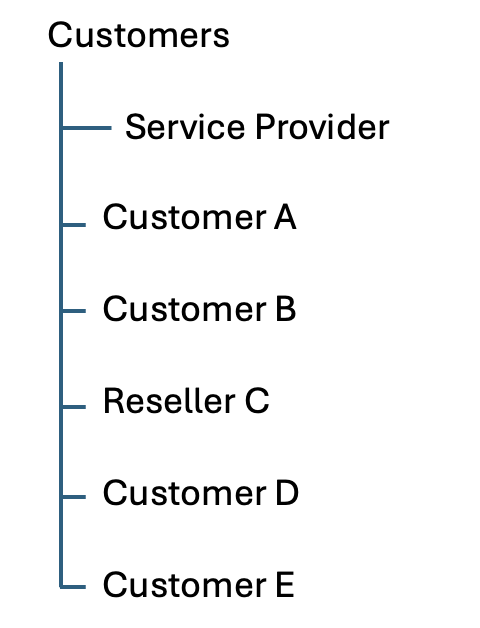
Other hierarchy options are available to suit different business needs. For more details and configuration guidance, see OU Hierarchy.
If you experience any issues or require any assistance with this process, please contact us at support@getatria.com.