Workspace Usage Examples
Overview
the purpose of this page is to show you examples and use cases of Workspace intended to improve your understanding of the different Workspace components how you can use them in your own configuration.
Each example is divided into a few sections:
- Scenario: To give context to the example.
- Component Setup: This sections provides the info on how you would configure the example using Workspace components.
- Atria User Assignment View: This shows how you would interact with the configuration in Atria.
- Outcome: The final section will provide information about the benefits of the setup.
If you have any further questions about the Workspace service or would like one of our engineers to give you a demonstration, please contact us at support@getatria.com.
Example 1: Retail Store – List-Based Setup
Scenario
A national retail chain needs an efficient way to manage access for store employees across multiple locations.
- Sales Associates need Point-of-Sale (POS) systems, training resources, and employee perks.
- Store Managers require additional permissions, such as inventory management and office access.
Since each store might have slightly different requirements, Workspace Lists are assigned at the store (customer) level.
- Admins then assign specific items to users from the pre-approved list, ensuring they get only the tools they need.
How Workspace Components Are Used
-
Item Types:
- POS Systems
- Training Resources
- Employee Perks
- Security Groups
-
Workspace Items:
- POS Systems
- "Retail Checkout System"
- "Store Inventory Scanner"
- Training Resources
- "Retail Training Portal"
- "Cyber Security Training Portal"
- Employee Perks
- "Employee Discount Access"
- "Gym Membership Discount"
- "Salary Sacrifice Scheme"
- Security Groups
- "Store Employee Group"
- "Retail Manager Access"
- POS Systems
-
Lists (Assigned to Customers – The Store Locations):
- "Retail Store – Standard Access" (POS, Training Portal, Employee Discount)
- "Premium Retail Store – Extra Benefits" (Adds Gym Membership Discount and Salary Sacrifice Scheme)
Atria User Assignment View
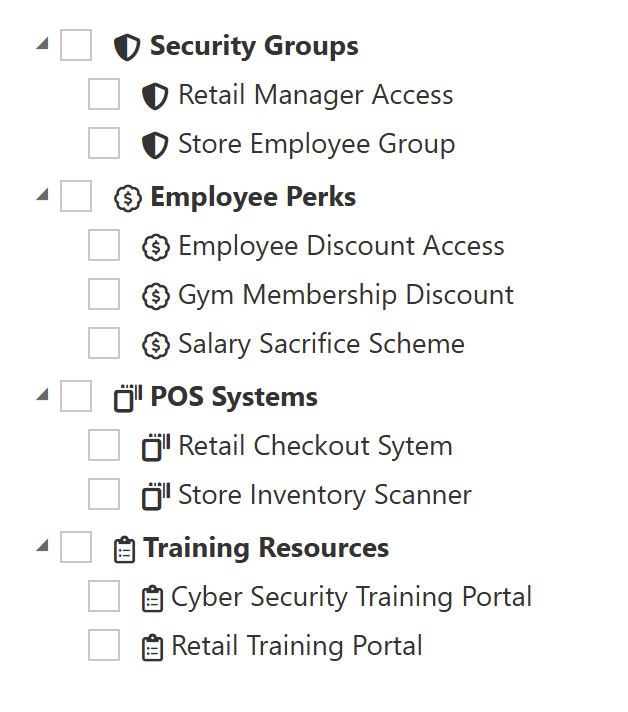
Outcome
- A new Sales Associate can be given different items dynamically based on their role.
- Admins select only the necessary items, ensuring each user gets a tailored set of permissions.
- Customers (store locations) are provisioned with the correct list during setup.
- Standard stores receive "Retail Store – Standard Access".
- Premium stores receive "Premium Retail Store – Extra Benefits", adding exclusive perks.
- During user assignment, items are grouped by their item type (POS Systems, Training, Employee Perks, Security).
- This simplifies navigation and selection for administrators.
- This setup allows for flexible user access, ensuring that each employee receives the right tools without unnecessary permissions.
This list-based approach enables efficient store setup while ensuring employees receive only the resources they need, reducing complexity for administrators.
Example 2: Hospital – Role-Based Setup
Scenario
A large hospital needs to streamline nursing staff access to critical systems.
- General Nurses require access to electronic medical records (EMR), communication tools, and security groups.
- Critical Care Nurses need additional permissions, including emergency response access and remote desktop capabilities.
Previously, IT had to manually assign each permission, leading to delays and errors. Now, using Workspace Roles, nurses receive access automatically when assigned a role, ensuring faster onboarding and security compliance.
How Workspace Components Are Used
-
Item Types:
- Clinical Applications
- Security Groups
- Communication Tools
- Patient Data Access
-
Workspace Items:
- Clinical Applications
- "Electronic Medical Records (EMR) - Nurses"
- "Pharmacy Access"
- Security Groups
- "Hospital Staff Security Group"
- "Emergency Response Team"
- Communication Tools
- "Nurse Chat System"
- "Paging System"
- Patient Data Access
- "Secure Patient Record Access"
- "Restricted Lab Results Viewer"
- Clinical Applications
-
Roles:
- "General Nurse"
- EMR Access, Nurse Chat, Paging System
- "Critical Care Nurse"
- All General Nurse permissions + Emergency Response Team + Secure Patient Record Access
- "General Nurse"
Atria User Assignment View
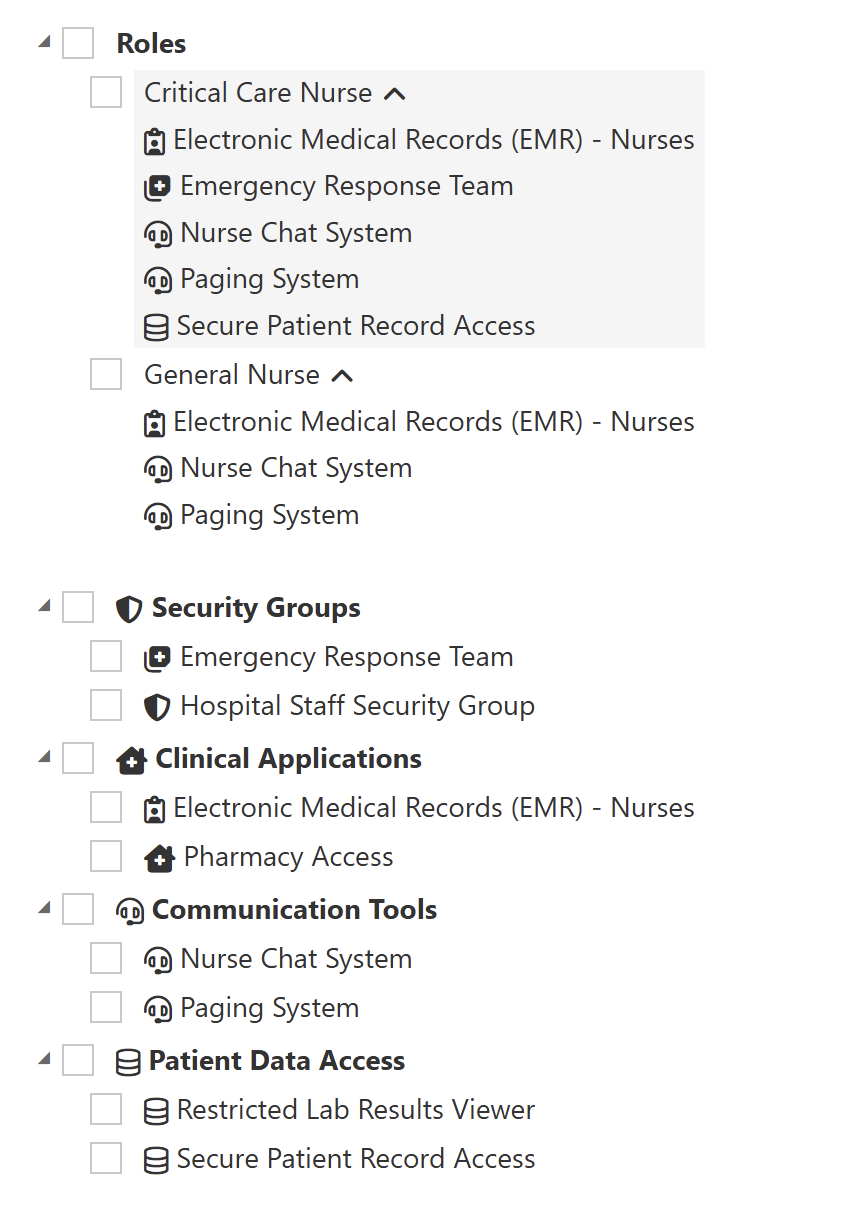
Outcome
- Admins assign broad roles instead of selecting multiple individual items.
- Faster onboarding with fewer manual errors.
- Items are grouped into clear categories (Clinical Applications, Security, Communication, Patient Data Access).
- Easier for admins to navigate and assign access.
- Role-based access ensures consistency across all users.
- Updates to a role apply automatically to all assigned nurses.
This role-based approach improves efficiency, security, and patient care by ensuring nurses receive the right access instantly without IT intervention.
Example 3: IT Department – Hybrid Setup with Roles and Application-Specific Items
Scenario
The hospital IT department needs a structured approach for managing access across multiple IT systems, including Citrix-based desktops and applications.
Some IT staff require full admin privileges, while others only need access to specific Citrix-managed apps or monitoring tools.
To handle this complexity, they use a hybrid setup where:
- Roles define broad permissions (e.g., "Network Engineer," "Citrix Desktop").
- Application-specific permissions are assigned separately (e.g., Active Directory Admin, VPN Viewer).
How Workspace Components Are Used
-
Item Types:
- IT Infrastructure
- Security Groups
- Remote Access
- Monitoring Tools
- Citrix Desktop
-
Workspace Items:
- IT Infrastructure
- "Active Directory Admin"
- "Active Directory User Viewer"
- "Server Admin"
- Security Groups
- "IT Security Group"
- "Network Admins Group"
- Remote Access
- "Hospital VPN - IT Staff"
- "Secure Shell Access (SSH)"
- Monitoring Tools
- "IT Monitoring Dashboard - Admin"
- "IT Monitoring Dashboard - Viewer"
- Citrix Desktop
- "Private Desktop Allocation" (Assigns a private Citrix desktop)
- "Secure Remote Application - Finance App"
- "Enterprise Browser Controls & Access"
- "WEM Profile Management for App Deployment"
- "Netscaler Policy - Social Media Access"
- "Citrix Monitor Reporting Access"
- IT Infrastructure
-
Roles:
- "IT Service Desk" (User Viewer, Basic Remote Access, Service Desk Dashboard)
- "Network Engineer" (IT Security Group, VPN, SSH, Monitoring Dashboard)
- "Citrix Desktop User" (Private Desktop, Secure Finance App, Browser Controls, WEM Profiles)
Atria User Assignment View
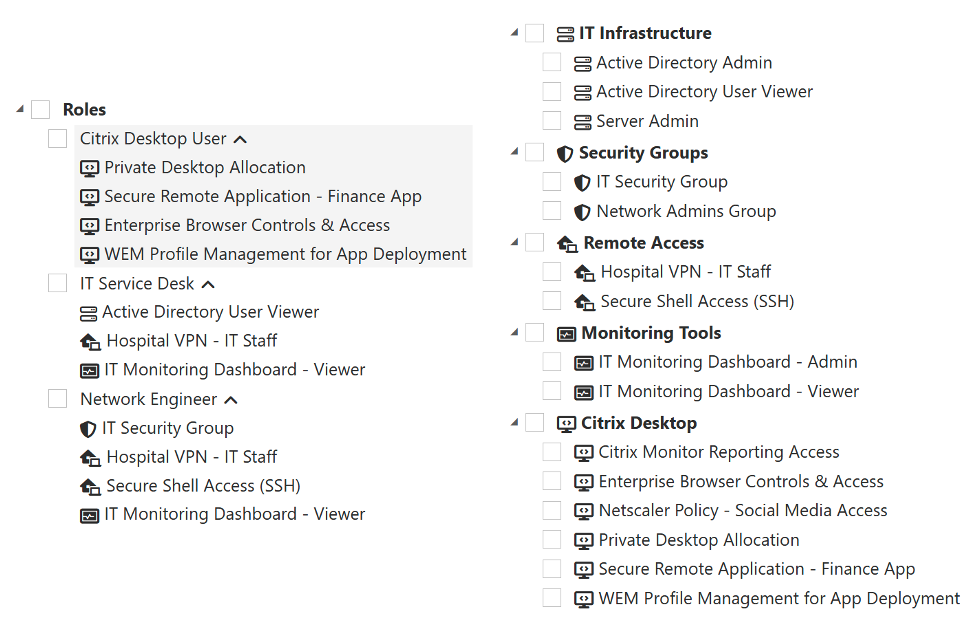
Outcome
- Admins can assign broad roles (IT Helpdesk, Network Engineer, Citrix Desktop) quickly, without manually picking individual items.
- Items are grouped logically under IT Infrastructure, Security, Remote Access, Citrix Desktop, and Monitoring—so admins don’t have to search for items manually.
- The Citrix Desktop Role ensures users automatically receive their private desktops and app permissions, while still allowing customization for additional needs.
- Marketing users can have restricted browser access via Netscaler Policies, ensuring security compliance while allowing social media access where needed.
- IT Admins managing Citrix environments can be granted monitoring access separately, ensuring least privilege access control.
For example:
- A Helpdesk Technician would receive the IT Helpdesk Role, which includes only basic remote access and limited viewing permissions.
- A Network Engineer gets the full set of networking tools, including VPN and Secure Shell (SSH) access.
- A Finance User working in Citrix would be assigned the Citrix Desktop Role, automatically granting access to a private virtual desktop, finance applications, and browser controls.
This hybrid approach makes Citrix-based access management seamless, ensuring that IT can enforce security while still enabling flexibility for different teams.
Example 4: Finance Firm – Advanced Role-Based Access with Security Automation
Scenario
A finance firm enforces strict security policies to ensure accountants, senior finance staff, and auditors have the correct access while maintaining compliance.
- Junior Accountants need access to basic accounting software and financial reports.
- Senior Accountants require additional permissions, including secure VPN and regulatory compliance access.
- Finance Administrators need full system control, including encrypted file access and security training.
To manage these requirements, Workspace Roles and Automations are used to:
- Standardize access across roles without requiring manual selection.
- Ensure security policies are applied automatically when users are assigned or removed from a role.
How Workspace Components Are Used
-
Item Types:
- Financial Software
- Security Groups
- Compliance Training
- Remote Access
-
Workspace Items:
- Financial Software
- "Accounting & Payroll System"
- "Financial Reports Database"
- Security Groups
- "Finance Department Security Group"
- "Regulatory Compliance Group"
- Compliance Training
- "Financial Fraud Awareness Training"
- "Data Handling & Privacy Training"
- Remote Access
- "Secure VPN - Finance Team"
- "Encrypted File Access"
- Financial Software
-
Roles:
- "Junior Accountant"
- Payroll System, Reports Database, Compliance Training
- "Senior Accountant"
- All Junior Accountant permissions + Secure VPN + Regulatory Compliance Group
- "Finance Administrator"
- Full access, Encrypted File Access, Data Handling & Privacy Training
- "Junior Accountant"
-
Automation Triggers for Security Policies:
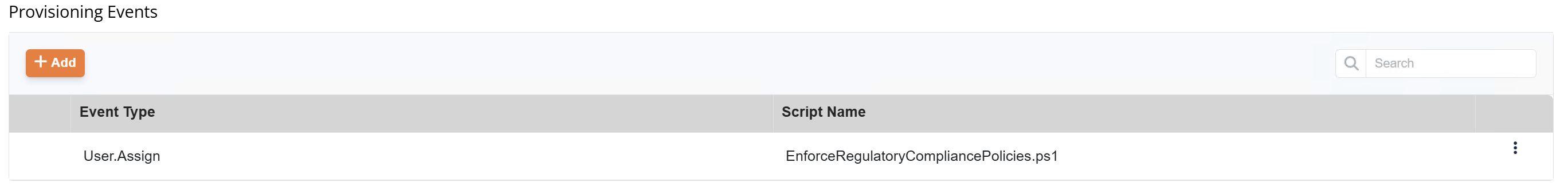
- On user.assign (Adding 'Finance Department Security Group' to User):
- Assign Finance Department Security Group
- Run PowerShell script to enforce regulatory compliance policies.
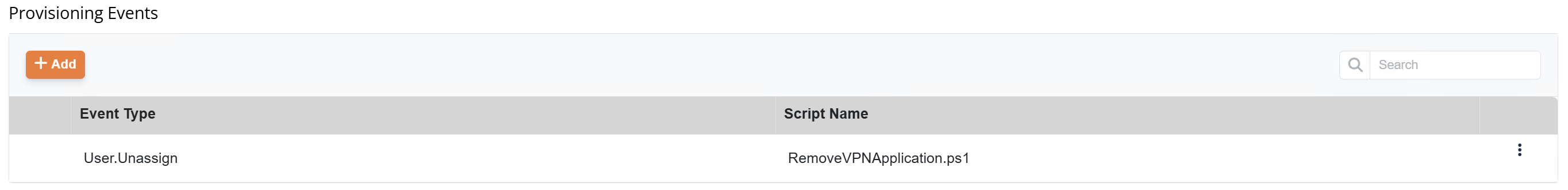
- On user.unassign (Removing 'Secure VPN' from User):
- Remove access to Secure VPN - Finance Team Security Group.
- Run PowerShell script to disable and remove Secure VPN application.
- On user.assign (Adding 'Finance Department Security Group' to User):
Atria User Assignment View
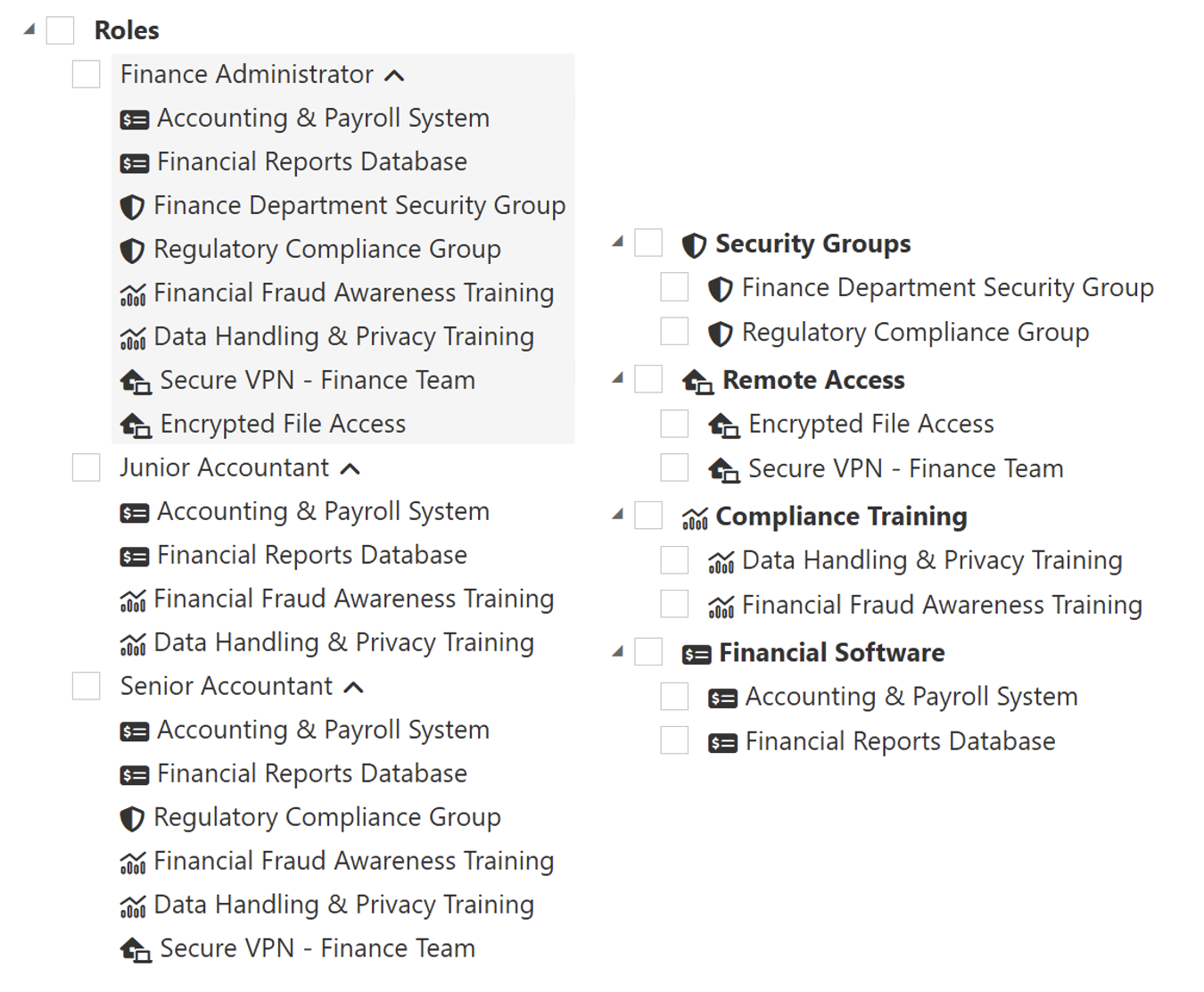
Outcome
- Users receive the correct financial tools dynamically based on their role.
- A Junior Accountant only gets basic tools, while a Finance Administrator receives full access.
- Customers (finance teams) are provisioned with the right roles during setup.
- This ensures consistent policy enforcement across all finance users.
- During user assignment, items are grouped by their item type (Financial Software, Security, Compliance, Remote Access).
- This makes it easy for admins to navigate and allocate permissions.
- Automations improve security and compliance.
- When a user is assigned a role, compliance policies and access permissions are applied instantly.
- If a user leaves, their access is revoked automatically, reducing security risks.
This role-based approach with automation ensures security, compliance, and efficiency, allowing finance teams to operate without delays while protecting sensitive data.
Summary
This page should have helped you understand the use case of Workspace, and how you can use the various components to setup your own environment. If you would like any more explanation of Workspace and how it can improve you business practices, please contact us at support@getatria.com.
The next few pages in this section will take you through the deployment of Workspace, and the setup of ItemTypes, Items, Lists, Roles, and Workspace Automation.