How to Enable AzureAD Authentication in Atria
Overview
This guide walks you through the process to enable AzureAD authentication when logging into the Atria Platform.
Prerequisites
- Customers must be provisioned with the AzureAD and MSOL services.
- MSOL must be provisioned to at least one user.
Diagram
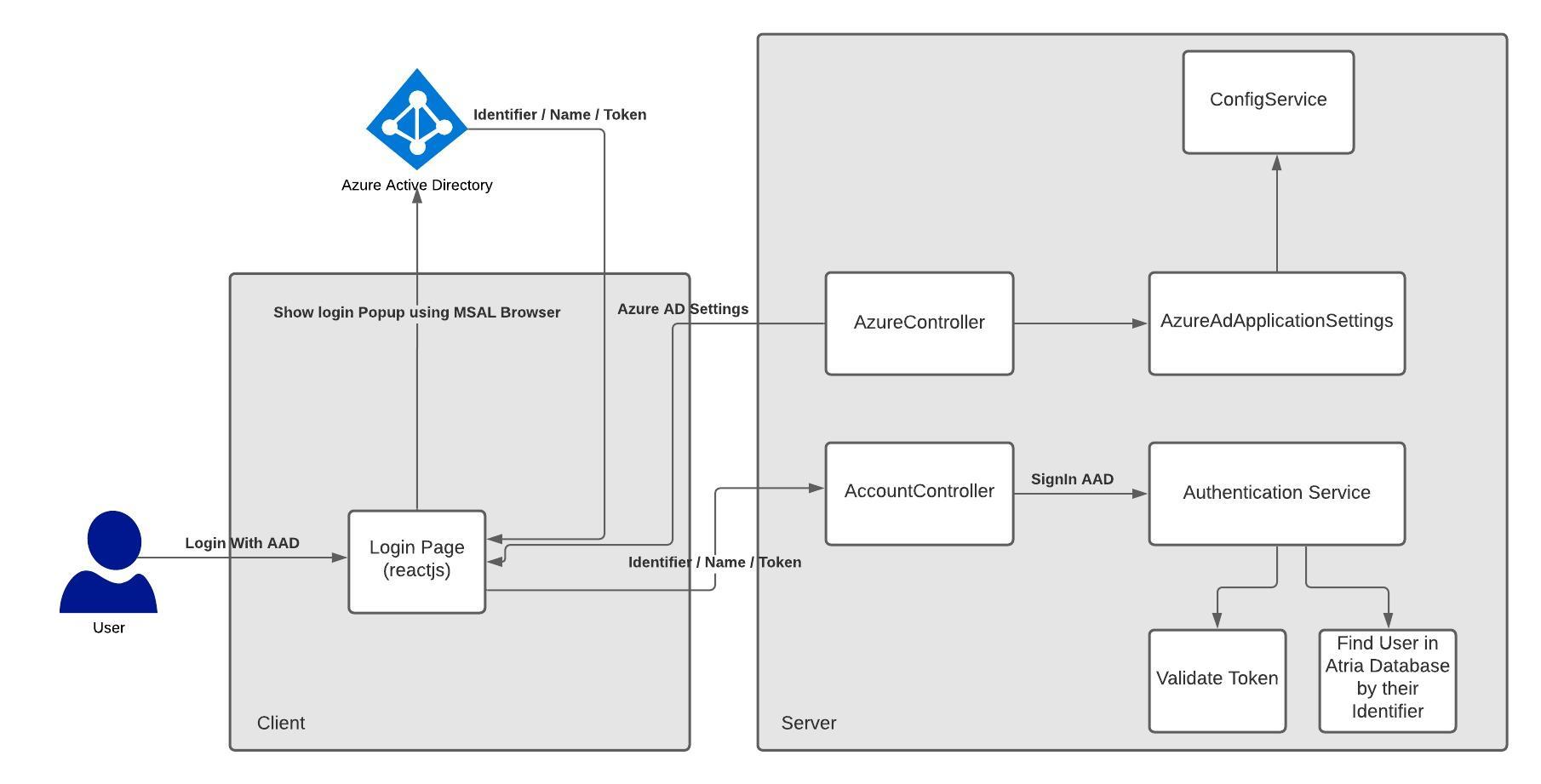
Process
Azure AD App Registration
-
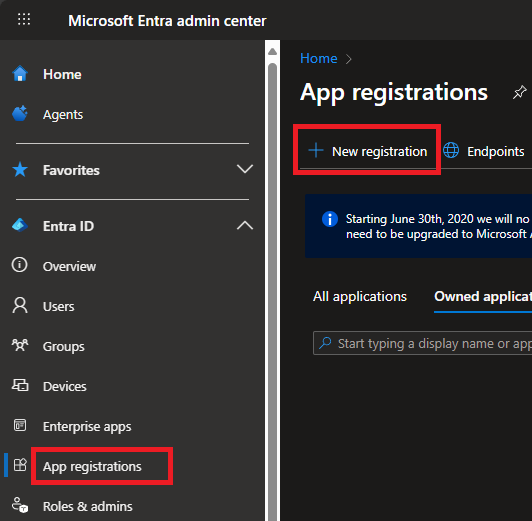
Login to https://entra.microsoft.com
-
In the sidebar menu, click on App registrations and then New registration:
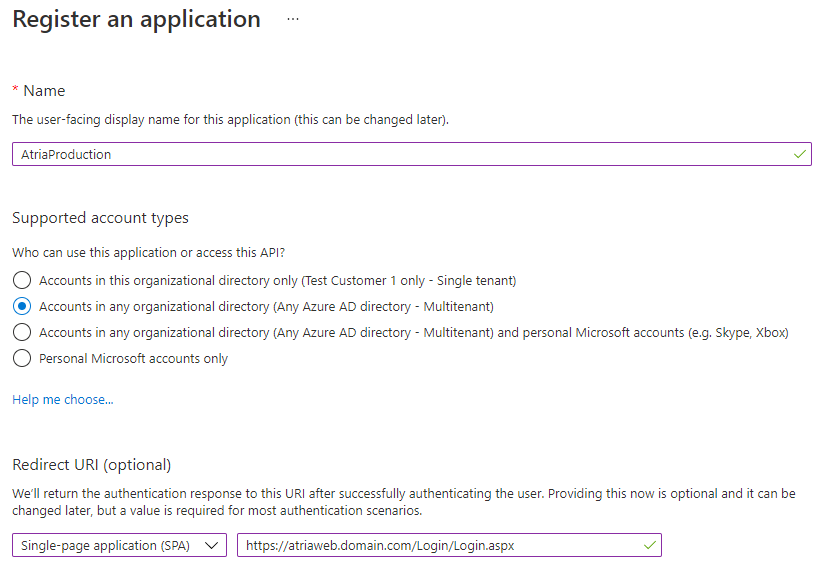
- Fill out the registration form:
- Name: Application name that will connect through this service e.g. 'AtriaProduction'.
- Supported account types: Select 'Accounts in any organizational directory (Any Azure AD directory - Multi-tenant)'
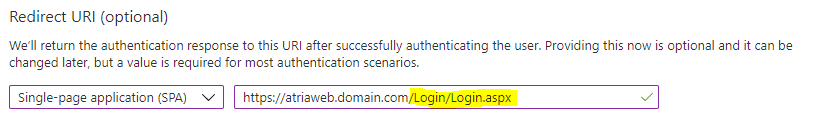
- Redirect URI: Select 'Single-page application (SPA)' and type your Atria login URL e.g. 'https://atriaweb.domain.com/Login/Login.aspx'
This field is case sensitive so we recommend to copy the URL from the browser when you navigate to the Atria login page.
-
Click Register.
-
Take note of the Application (client) ID as it will be used later:
Get ConfigService Parameter Values from Web Server
On your Web Server:
- Open file C:\inetpub\Automate101\Atria\WebForms\bin\appsettings.Customer.json and look for the below value:
- Execute powershell below:
Get-AtriaAppSettingsSecrets -AppSettingsFile C:\inetpub\Automate101\Atria\WebForms\bin\appsettings.Secrets.json
- and look for the below values:
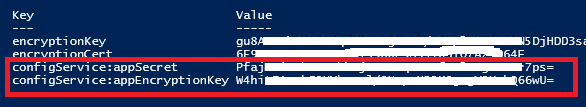
- Take note of these 3 values as they will be used later.
Configure the Atria Platform to Use AzureAD Authentication
-
Below are the configuration keys and values that will be added to ConfigService:
-
AzureAd_ClientId: The Application (client) ID of the app registration from previous step e.g.
8*******-****-****-****-********913d. -
AzureAd_TenantId: Static value is 'organizations'.
-
AzureAd_RedirectUri: Atria login page e.g. '/Login/Login.aspx'.
-
-
AzureAd_PostLogoutRedirectUri: Same as AzureAd_RedirectUri e.g. '/Login/Login.aspx'.
-
AzureAd_ShowPIILogs: This is a flag by which show if showPII needs to be enabled in log or not. By setting it to 'true' the system produces more details for Azure AD Authentication in case there is an error. By default, it is 'false'.
-
On your Provisioning Server:
-
Launch an administrative Powershell session.
-
Execute the below commands to apply the values to Atria ConfigService:
Set-AtriaConfig -ConfigKey 'Configuration key' -ApplicationId 'configService:appId value' -ApplicationSecret 'configService:appSecret value' -AppEncryptionKey 'configService:appEncryptionKey value' -ConfigValue 'Configuration value'
Example:
$EntraApplicationId = "8*******-****-****-****-********913d"
$ConfigSvcAppId = "42******-****-****-****-*******9fec5"
$ConfigSvcAppSecret = "qW***zcz4="
$ConfigSvcAppEncryptionKey = "nJ***MnmE="
Set-AtriaConfig -ApplicationId $ConfigSvcAppId -ApplicationSecret $ConfigSvcAppSecret -AppEncryptionKey $ConfigSvcAppEncryptionKey -ConfigKey 'AzureAd_ClientId' -ConfigValue $EntraApplicationId
Set-AtriaConfig -ApplicationId $ConfigSvcAppId -ApplicationSecret $ConfigSvcAppSecret -AppEncryptionKey $ConfigSvcAppEncryptionKey -ConfigKey 'AzureAd_TenantId' -ConfigValue "organizations"
Set-AtriaConfig -ApplicationId $ConfigSvcAppId -ApplicationSecret $ConfigSvcAppSecret -AppEncryptionKey $ConfigSvcAppEncryptionKey -ConfigKey 'AzureAd_RedirectUri' -ConfigValue "/Login/Login.aspx"
Set-AtriaConfig -ApplicationId $ConfigSvcAppId -ApplicationSecret $ConfigSvcAppSecret -AppEncryptionKey $ConfigSvcAppEncryptionKey -ConfigKey 'AzureAd_PostLogoutRedirectUri' -ConfigValue "/Login/Login.aspx"
Set-AtriaConfig -ApplicationId $ConfigSvcAppId -ApplicationSecret $ConfigSvcAppSecret -AppEncryptionKey $ConfigSvcAppEncryptionKey -ConfigKey 'AzureAd_ShowPIILogs' -ConfigValue "true"
Once this has been completed, you should see the Sign in with Microsoft button on the Atria login page:

Configure Proxy / Load Balancer (Optional)
If there is a Load Balancer or Reverse Proxy configured in the target environment, the following headers must be defined and pass to the downstream proxies in order for the Azure AD authentication to work.
- X-FORWARDED-HOST: The hostname and the port number (e.g. atriaweb:8086)
- X-FORWARDED-PROTO: The protocol which can be 'http' or 'https'
Here is an example for defining these headers in nginx reverse proxy:
location / {
proxy_pass http://localhost/;
proxy_set_header X-FORWARDED-HOST $http_host;
proxy_set_header X-FORWARDED-PROTO $scheme; # This can be omitted if proxy is referencing to http to internal web server port i.e. https --> http
}