Configuring Microsoft Online with ADFS
Objective
This article provides a guide to configuring Active Directory Federation Services (ADFS) in preparation for integrating it into the Atria Microsoft Online Service.
Prerequisites
- Domain joined Windows Server host.
- Publicly accessible FQDN associated with public IP (Example:.yourdomain.com).
- Valid SSL certificate associated with site FQDN (Wildcards are supported).
- Port 443 open inbound and outbound on public IP associated with ADFS FQDN.
Process
-
Setup and Configure Federation
- Deploying a Federation Server Farm - Deploying a Federation Server Farm | Microsoft Learn
- If planning to have ADFS Proxies - Deploying Federation Server Proxies | Microsoft Learn
-
When configuring the ADFS service, the service account must be an account that has permission to read object properties under the CustomersOU which can be specified in Atria. If ADFS service is running with the service account created automatically by Windows, it does not have the proper permissions to read “CustomersOU”.
The solution is to add the AD FS service account into the CortexReadOnly group:
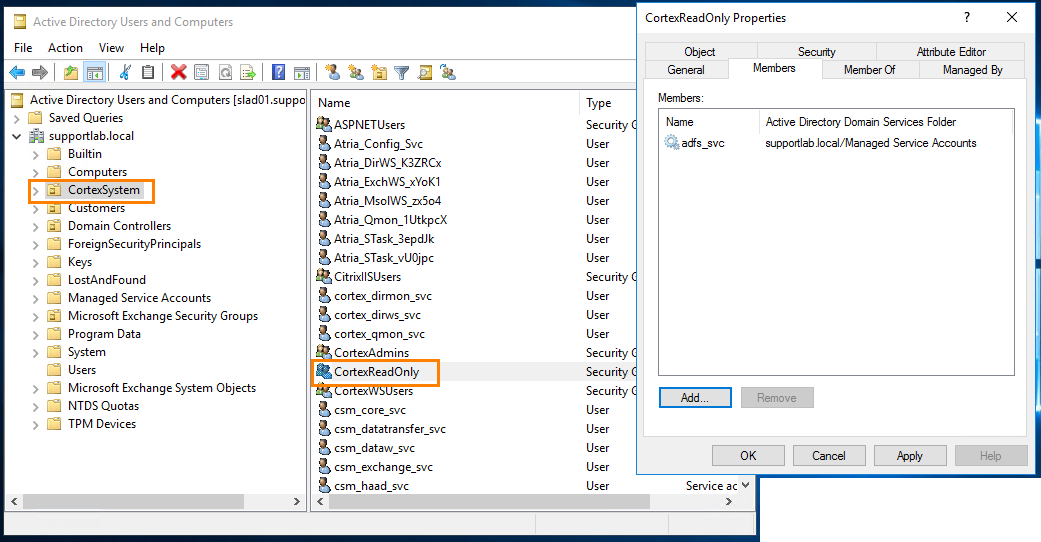
Another option is to use an existing Atria service account which has that permission. It can be used to run the AD FS service.
Verifying that your domain is not yet federated
Make sure that your PowerShell session is on TLS 1.2:
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12
- On your Primary ADFS server, open an Administrator PowerShell window and Install the MSOnline module:
Install-Module -Name MSOnline
- Import the MSOnline module:
Import-Module MSOnline
- Connect to your Azure AD Tenant:
Connect-MSOLService -> Enter your Azure AD credentials on the pop-up
- Once you are connected to your Azure AD Tenant, let's make sure your domain is currently recognized as a "Managed" domain:
Get-MsolDomain -Domainname domain.com -> Should show your domain as "Managed"
- Now we can make sure that the domain you are converting is currently NOT in the ADFS configuration:
Get-MsolFederationProperty -Domainname domain.com -> Should show that domain does not exist in the configuration
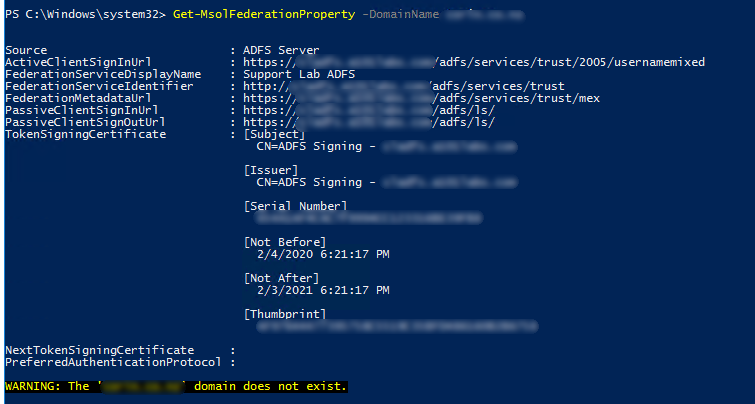
You may take note of the above properties as this can be copied over when doing the MSOnline ADFS Policy within the Atria Portal
Now that we have connected to the Azure AD Tenant and confirmed that are domain configured as Managed, we can convert it to a "Federated" domain. When done, all of your Azure AD sync'd user accounts will authenticate to your on-premises Active Directory via AD FS.
- While still on your AD FS server, import the ADFS module:
Import-Module ADFS
-
Convert your domain for it to be federated:
- If you have a single top-level domain, you do not need to include the -SupportMultipleDomain switch.
Convert-MsolDomainToFederated -DomainName domain.com- If planning to support multiple domains:
Convert-MsolDomainToFederated -DomainName domain.com - SupportMultipleDomain -> (A successful updated message should be your result)
Once this has completed, we can see the properties for the converted federation. You will also notice that the PreferredAuthenticationProtocol is now set to WsFed
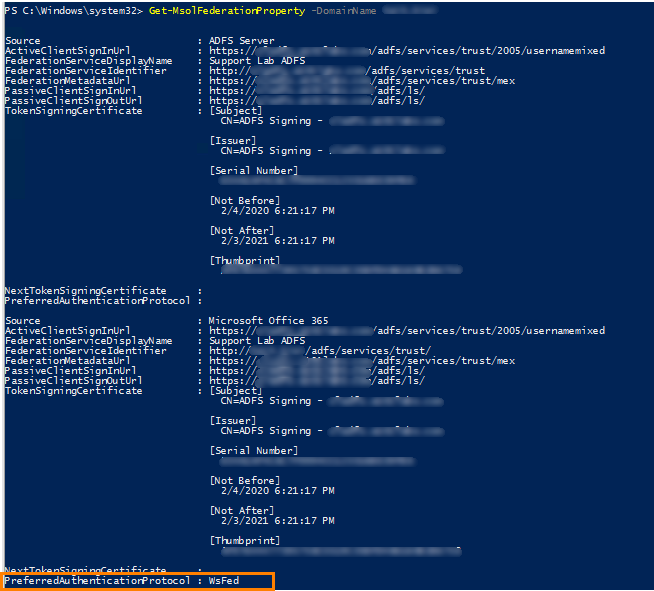
- During the federation, it will also create the Relying Party Trusts for Microsoft Office 365 Identity Platform Worldwide.
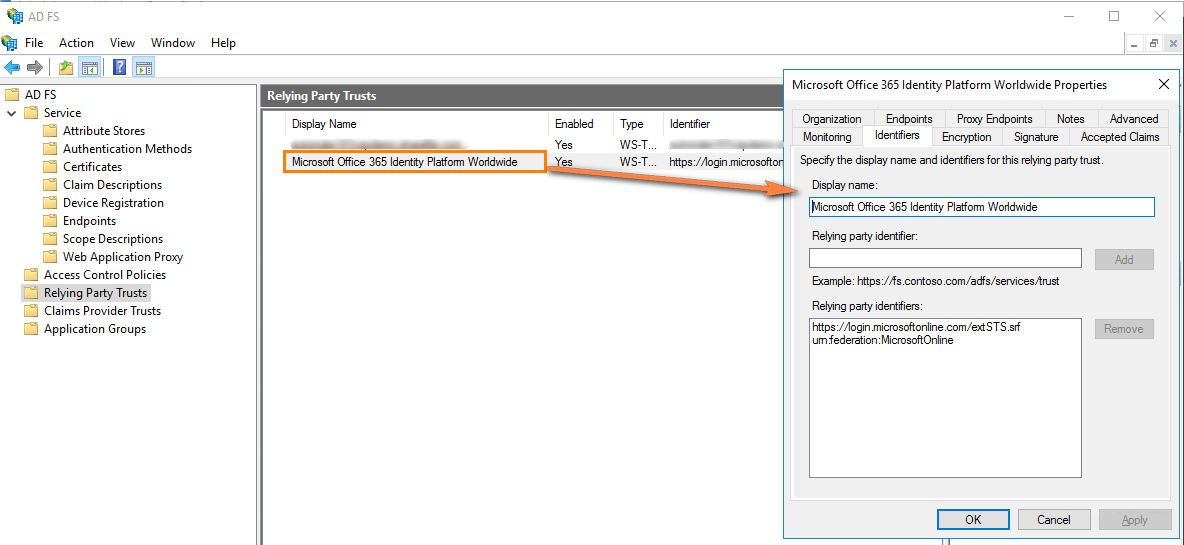
Your ADFS server is now set up to federate for Microsoft Online. It is now ready to be used within the Atria platform.
Configure the Microsoft Online ADFS Policy in Atria
- On the Atria Portal, navigate to
Services > Microsoft Online > ADFS Policies. - Create a New ADFS Policy and input the necessary details. Most of the values here can be retrieved from the MSOLFederationProperty from the previous steps.
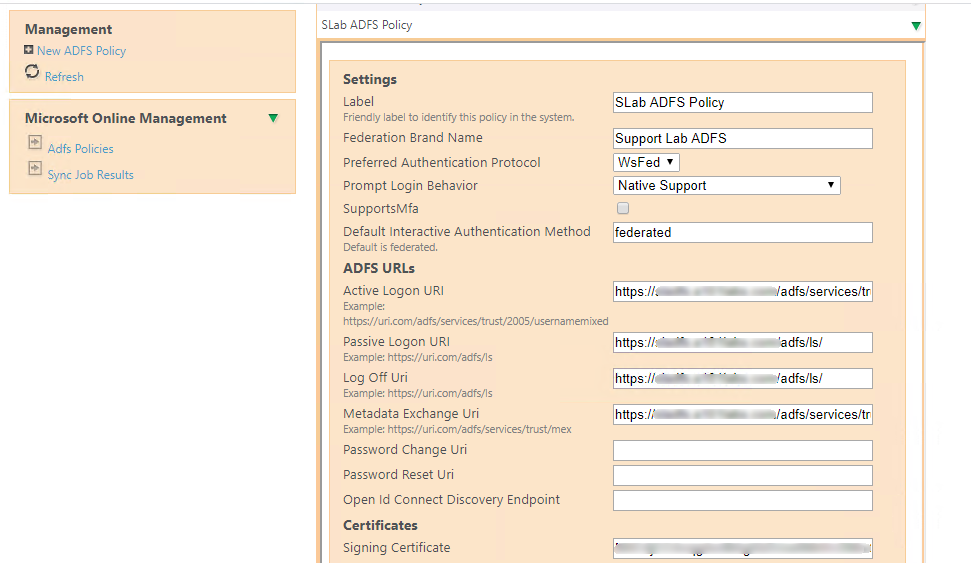
The signing certificate can be retrieved using the Base64 encoding value of the SSL certificate used on the ADFS server.
- Once the ADFS policy has been saved, this can then be selected on Azure AD service customer plans, you may create a new customer plan to handle the Tier License Management and the ADFS.
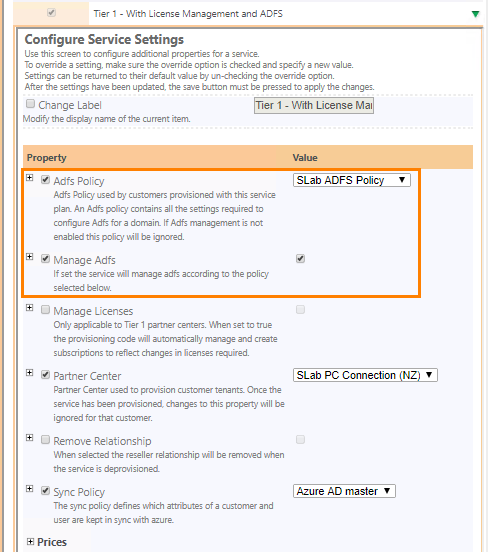
Make sure that when you setting up the customer plan with ADFS enabled, both the ADFS Policy and the Manage ADFS must be enabled.
Customer Provisioning - Microsoft Online with ADFS
When provisioning the Azure AD service, make sure that the domain that is federated will be ticked as "ADFS Enabled":
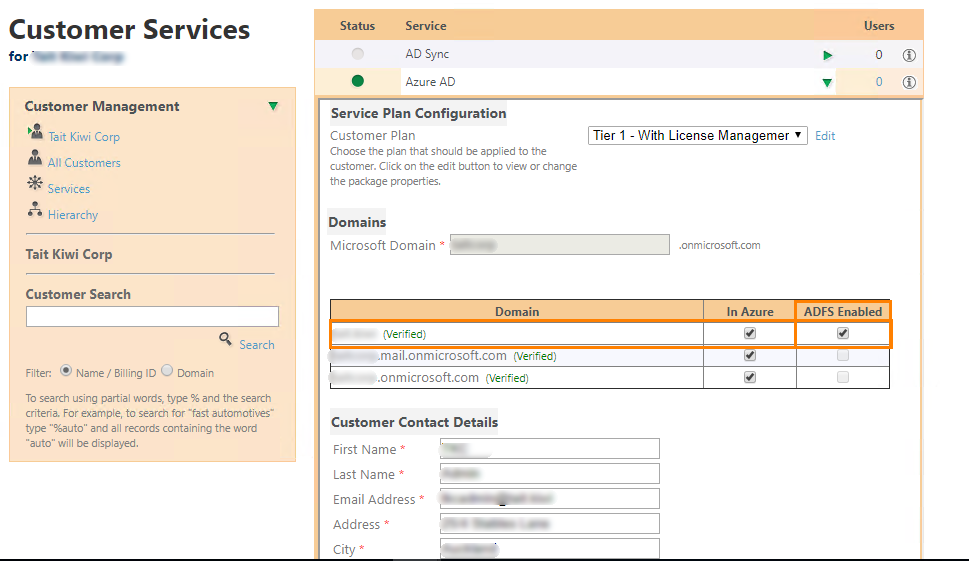
Now that this is configured on a customer, any user under it that will be provisioned with Microsoft Online service will use the Federation Service for authentication.