GPO Configuration for Atria
Overview
Atria provisions permissions within Active Directory (AD) to support the assignment of Group Policy Objects (GPOs) to restricted customer Organizational Units (OUs).
This document outlines how permissions must be configured for GPO assignment to work reliably in Atria-managed environments.
AD Structure Example
The following is an example of a permission structure that supports GPO assignment to customer-specific OUs:
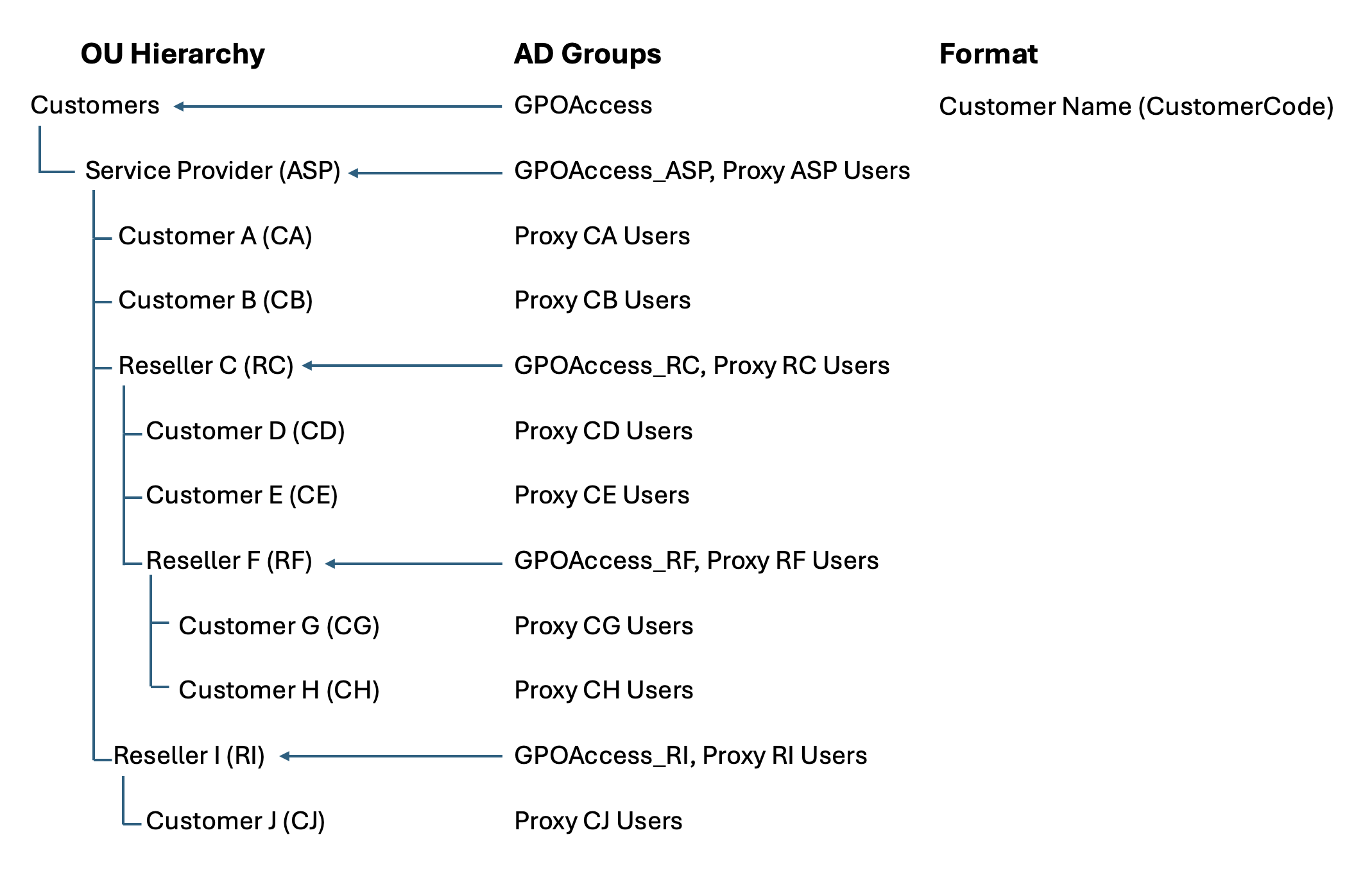
GPOAccess Group Permissions
The GPOAccess groups are assigned read/traversal-level permissions on the relevant OUs. These enable GPO application while restricting broader access.
| Permission | Definition | Active Directory Definition |
|---|---|---|
| Deny - List Contents | Prevents viewing of the contents of the OU and its descendant objects | Prevents users from seeing files or subfolders inside the OU. |
| Allow - List Object | Allows viewing of the OU itself | Users can see the OU exists, but cannot access contents. |
| Allow - Read all properties | Allows reading of all properties of the OU | Users can view metadata (e.g., name, timestamps), but not modify anything. |
- These permissions enable GPO application without exposing sensitive data or OU structure.
Proxy User Group Permissions
Proxy (CustomerCode) Users groups are used to grant read access for GPO application and filtering.
| Permission | Definition | Active Directory Definition |
|---|---|---|
| Allow - Read | Allows reading of the OU and its descendant objects | Grants visibility into contents of the OU and subfolders, without permission to modify them. |
Traversal and Inheritance
To ensure GPOs reach the correct user objects:
GPOAccessgroups must provide "Read all properties" and "List object" access through each level of the OU hierarchy.- This allows traversal of "broken inheritance" structures.
- Permissions above the customer OUs are typically granted to the Authenticated Users group.
Microsoft Security Patch: MS16-072
With the release of MS16-072, Microsoft enforced stricter security rules for GPO processing:
Requirements Post-MS16-072�
The computer object must have:
- Read access to the GPO
- Read access to the user object
Without these, the GPO will not apply.
Recommended Configuration
To comply with the above and ensure GPOs apply:
- Manually assign read access on the GPO
- Add the computer object to the relevant
Proxy (CustomerCode) Usersgroup - Assign the GPO to that Proxy group using Security Filtering
Advanced: Restrictive Filtering
If you need tighter control:
- Create a separate group containing only specific users
- Add that group to the
Proxy (CustomerCode) Usersgroup - Apply the GPO to this new, filtered group
Summary
- Use GPOAccess groups to provide minimal traversal access
- Use Proxy groups to ensure computers and users can read the GPO
- MS16-072 requires you to explicitly grant read access to GPOs
- Always test permission propagation across broken inheritance trees
If you require any assistance or experience and errors with this process, please contact us at support@getatira.com.